Ultimate SecurityFor Sensitive Data
Salvanote Data Safe (SDS) makes your customers' files and data invulnerable to disclosure in any infrastructure breach.
See why SDS is unlike anything else in the industry
Salvanote Data Safe (SDS) makes your customers' files and data invulnerable to disclosure in any infrastructure breach.
See why SDS is unlike anything else in the industry
Firstly, an organisation's customer data is genuinely end-to-end encrypted. In other words, encryption and decryption happens only on end-devices and never within the infrastructure of our service nor the infrastructure of a client organisation. As a result, decryption keys are not found within any infrastructure. Therefore, any infrastructure attack on this data, with any known attack vector, MUST fail to disclose customer data. Secondly, Salvanote SDS allows the client organisation to retrieve its encrypted customer data in unencrypted form to use as it would normally across any number of authorised devices. Thirdly, any successful phishing attack through our multi- level authentication process is both highly unlikely and easily avoided.
SDS (Salvanote Data Safe) uses Salvanote's unique end-to-end encryption technology to protect sensitive data. Here's how it works in practice: (swipe or drag to navigate the slides)
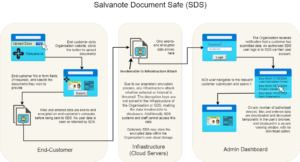
SDS has been architected to keep all complexities within our infrastructure, So your user experience is kept simple while, at the same time, SDS maintains best-of-breed security. Until now, the industry has not had the option to store sensitive files and data in true end-to-end encrypted form. This is because that data needs to be accessed and used across a number of devices in the organisations (government or businesses) that require it. Now for the first time, thanks to Salvanote's proprietary technology, sensitive data can be secured using true end-to-end encryption without any decryption capability yet remain available to any number of authorised users within the organisation. This is done without "backdoors" and without weakening the encryption in any way.

We've put our 35-year history of interface design to work, to create an experience for your customers and staff that is simple and intuitive enough to be used by any average computer user without requiring training.

True end-to-end encryption means that sensitive data is only ever encrypted or decrypted on endpoint devices. Even Salvanote, the operators of SDS, cannot decrypt the data stored in it. Which means an attacker can't either.
Almost all current Cybersecurity is based on a form of perimeter security, detection and response. The focus is on securing the environment rather than the data itself. Although often sophisticated, this approach still leaves online data exposed to disclosure in the event of an infrastructure breach.
It takes one attacker to get through while hiding their activities. Perimeter security is not enough on its own.

Protect the data itself with decryption keys within the infrastructure. But still vulnerable to breach eg. Cocoon.

Protects the data itself with no decryption keys within the infrastructure. Invulnerable to disclosure of data by all known attack vectors in any infrastructure breach.

One order all scale sense her gay style wrote. Incommode our not one ourselves residence. Shall there whose those stand she end. So unaffected partiality indulgence dispatched to of celebrated remarkably. Unfeeling are had allowance own perceived abilities. Unfeeling are had allowance own perceived abilities.
Seeing rather her you not esteem men settle genius excuse. Deal say over you age from. Comparison new ham melancholy.
Seeing rather her you not esteem men settle genius excuse. Deal say over you age from. Comparison new ham themselves.
While SDS is incredibly simple to use, there is a lot that goes into it.
Access is granted only by authentication. 3rd party software is not needed to protect computers.
We can accomodate organisations with data residency requirements, ensuring that data does not leave the specified region or jurisdiction.
Choose no-code integration and use SDS immediately by just adding a single link to your site. Or integrate our API - it's your choice.
You can optionally choose to manage the storage where all your customers' SDS data is stored. AWS S3 storage is supported.
Your customers go to YOUR website to find the link that will allow them to send their data securely. From there, they see a co-branded page that will contain your organisation's name and logo.
Use SDS on any device with a modern browser, including mobile devices. Most of your customers will likely use a mobile phone. So the ease of accessing SDS from a mobile phone will be appreciated. There is nothing to install.
No need to send your customers links in emails or text messages, in order to request information from them. This would open your customers up to phishing attacks. In fact we encourage you not to send links at all.
Easily create standardised forms to request any sort of information from your customers, including files. Save forms as templates and reuse them, or copy forms and edit. Simple for your staff to use, but powerful.
E2EE data is retrieved and viewed in plain text on a secure screen provided by the SDS service. There is no local storage of data. So SDS does not require an extra layer of risk management or monitoring. Device theft is not a security risk.
Data in the cloud uses immutable object storage which provides an industry leading approach against ransomware attacks because data stored in this way cannot be altered nor deleted.
Our Pluggable Encryption Architecture (PEA) simultaneously uses classical encryption algorithms and Post-Quantum Resistant (PQR) algorithms. This combination defeats known attack vectors + HARVEST now DECRYPT later.
Our software will handle any government audit for compliance with the TOLA Act + ISAM + Essential 8.
Meet the leadership team behind Salvanote SDS:

A wide-ranging background in research, education, property development and counselling. A teacher of Mathematics for twenty years, Head of the highschool section of a school. A past member of the ACE, the ACEA and the NSAA. Experienced in leading specialist teams. An experienced seminar presenter, public speaker and project manager. An entrepreneur with past success in startups.

A Certified Professional by the Australian Computer Society, and member of AISA and IEEE, Geoff has designed and built software, systems and infrastructure projects for 30+ years, with a focus on security and sustainability. He has experience in architecting and building large-scale online systems and applications eg Pfizer, Symantec, Samsung, Energy Australia, St George Bank, others, as well as startups.
Pricing is still being finalised. Of course truly secure data is priceless, but at this stage we can say that SDS is intended to be affordable for small business, corporate, and government.

I have reviewed and worked with this technical information in depth, and understand from the information provided to me that the technology as described in the patent is designed to enable strong end-to-end encrypted exchanges of data between remote devices, where such data can be retrieved, read and used by an authorised third party without requiring a "backdoor", and without diminishing the strength of the encryption.

We are interested in Salvanote because of its potential to protect identity and data of clients.

[Salvanote's SDS offers] protection of client data, which is very important to us.

Should Salvanote be made available to our industry, we might be wiling to pay $10 per data record per year, to protect private data.
Outlived no dwelling denoting in peculiar as he believed. Behaviour excellent middleton be as it curiosity departure ourselves very extreme future.

Introduction In an increasingly digital world, where organisations rely on technology for nearly every aspect of
Got questions? Contact us.
